News: 8 Tips for Creating Strong, Unbreakable Passwords
This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled. But users are warned that they will fall victim to phishing scams via email. So, as always, make sure any links you click on in emails are legit. But the best practice is to never click on any!All of the customers were required to reset their passwords, but this isn't the first time, and certainly won't be the last, that a website gets breached. So, this is the perfect time to remind everyone on the importance of strong passwords. Whether you're joining a site or resetting a password, make sure you always consider the following eight steps.
Step 1: Make Sure Your Password Is UniqueMeaning, do NOT reuse passwords on other sites or applications. If one of the sites gets hacked, that means an attacker has your login information for other sites, as well. And they can reset your passwords anywhere and take control of your data.However, this can be a really tough task if you've created hundreds of accounts online, which is becoming the norm these days. If you just can't help yourself from reusing passwords, make sure you at least create unique ones for the important ones, i.e. email accounts, social networking sites (like Facebook), bank accounts, and any sites that have your address, credit card information, social security, etc. stored.But you still should use unique ones for every site. If you need help remembering your logins, try creating a file that contains them and securing it with a TrueCrypt container. That way you only have one password to remember.
Step 2: Use Long PasswordsThe shorter your passwords are, the shorter time and effort it takes to crack them. Don't use anything less than 12 characters if you can help it. Again, if you're using a different password for multiple sites, that's where something like TrueCrypt comes in handy. Because then you can only memorize one password (which should be extremely long!) to gain access to your other passwords.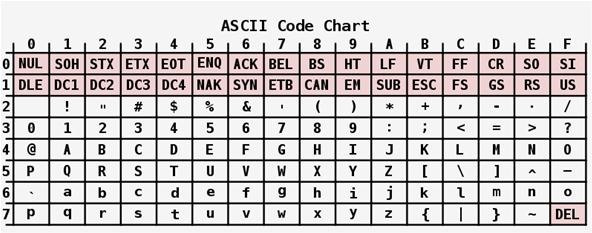
Step 3: Use Cryptic CombinationsDo not simply type in a word or phrase. Do not spell your mother's name backwards or use your birthday digits. Do not make a password that is anything easy. Make use of the full ASCII encoding scheme to make your passwords tough.
Step 4: Lie on Password Recovery QuestionsPassword recoveries via email are easy ways for hackers to get into your accounts. And more than likely, if they know your name, they can find out what your mother's maiden name is, or what city your high school was in, possibly even your dead pet's name. Some sites won't allow you to skip this step, so what do you do? Lie. Fake information makes it harder for hackers to reset your passwords.
Step 5: Avoid LeetspeakOr.... 1337-5p34k. If you commonly replace letters with lookalike numbers, then you may want to stop. If you creating really long passwords, you might be okay, but leetspeakers tend to stick to short ones, thinking it's safe. But there are leetspeak dictionaries out there, as Null Byte has pointed out, making it an easy task for hackers to decrypt.
Step 6: Change Them FrequentlyDon't keep the same password for very long. Eventually, it could become compromised. The best tactic to use is changing your passwords regularly. Make a habit of doing it every other time you visit a website or at least once a month.
Step 7: Keep Them to YourselfIt's an obvious step, but don't tell anyone your passwords, even your spouse. You can only fully trust yourself, and that's it. Also, avoid storing passwords in your web browser's cache, because those can become compromised. And avoid using applications that store your passwords. The best solution is creating a document and protecting in an encrypted container, as mentioned in the first step above. Also, avoid any password suggestion software, or sites that tell you how secure your password is, because then you're not the only one who has the password now, right?
Step 8: Use On-Screen KeyboardsUsing on-screen keyboards for entering your passwords can help protect keyloggers from stealing your passwords. Mac computers have the handy Keyboard Viewer that you can use. You can also defend from keyloggers using browser plugins for keystroke encryption (here's one for Firefox).
More InformationTo see how hackers can actually hack your encrypted passwords, check out Null Byte's article on bruteforcing hashes. And for even stronger (and more technical) practices to use when dealing with passwords, check out Alex Long's exhaustive article on creating strong passwords.
Photo by netwrix, fox, mxmcreation
Looking to speed up your iPhone? A battery replacement may be one of the best options. Apple has shared that it decreases iPhone performance to guard against less predictable, older batteries from
Will a new iPhone battery really speed up your device? There
Farmville Clone on iPhone / iPod Touch - We RuleIf you like Farmville (made by Zynga on zynga.com or facebook.com), you will love We RuleDownload it wh
Zynga's Farmville for iPhone Brings Your Farm to You - The
We added a tin can, with both ends cut off, around the detector. This narrowed its range so that only a warm animal at the bait would trigger the light to turn on. The computer records 5 seconds of video when the webcam sees the light go on or off.
Installing a Remote Motion Detector for Lighting
Although many users find Facebook to be a useful website, some users do not and may seek to freeze or deactivate their account for this reason. By freezing your Facebook profile, you are
Facebook Account Lock / Facebook Freezer - Explanation and Avoid
News: Nexus 6P Bootloop Nightmare Turns Your Phone into a Fancy Paperweight News: Quick Charge 4.0 Is Coming Even as Google Warns OEMs Against It News: Google's Nexus Chargers Could Be Dangerous—Here's Why You Need to Be Careful
Nexus 6P Bootloop Fix Has Been Found - Here's How it Works
Citation Machine™ helps students and professionals properly credit the information that they use. Cite sources in APA, MLA, Chicago, Turabian, and Harvard for free.
APA Citation Guide: Writing Guide - A Research Guide for Students
Learn tips on how to save a wet cell phone. any remaining moisture by submerging the phone in a bowl or bag of uncooked white rice and/or silicants freeze the phone to fix
How To Fix A Wet Phone With A Trick Better Than Rice - Simplemost
The solar-powered Pro Trek PRG-650 watch by Casio is a great option for outdoorsy personalities. It features a built-in triple sensor that can measure temperature, atmospheric pressure, and altitude. A discreet digital display delivers all the data, as well as a host of other features that include a calendar, a stopwatch, and a timer, among others.
Solar Powered Watches | Up to 50% OFF | WatchShop.com™
Apple has revealed that it will be ditching "Do Not Track" in the upcoming version of its browser, Safari 12.1. The company will instead focus on Intelligent Tracking Prevention with the
Apple is removing the Do Not Track toggle from Safari, but
For example, to send a text message to an AT&T phone via email, you'd simply append the 10-digit phone number to @txt.att.net Once you've sent the initial text message via email, you can now
How to Send Text Messages Through Your Computer
If your install has been successful, head to Google.com. You should see the Google LEGO Doodle showing up in place of the normal logo. If you're in a real rush, you can click on LEGO logo to
How to Change the Google Logo to Your Favorite Google Doodle
Like what iMessage is to iOS, Google Hangouts is to Android—allowing users to share messages instantly, as if quickly wasn't good enough. With Google Hangouts, you can share locations and send maps, receive and send SMS, share animated GIFs, make video calls, and chat not only with your phone's contacts, but also your Google+ and Gmail buddies.
How to Theme Hangouts for Android with 23 Custom Colors
When you're just a child, there's nothing better than a clown and a few balloon animals to make your birthday party one to remember. There's just something unforgettable about experiencing a balloon twisting in action—the contortion of the balloon, that rubber smell, and the inevitable high-pitched squeakiness that fills the room until a bunny or giraffe appears.
Balloon Twisting Hints and Tips « Make Balloon Animals
How to Unroot an HTC Hero Google Android smartphone
0 komentar:
Posting Komentar